Is cyber takedown the next generation of more effective counter-UAS technology?
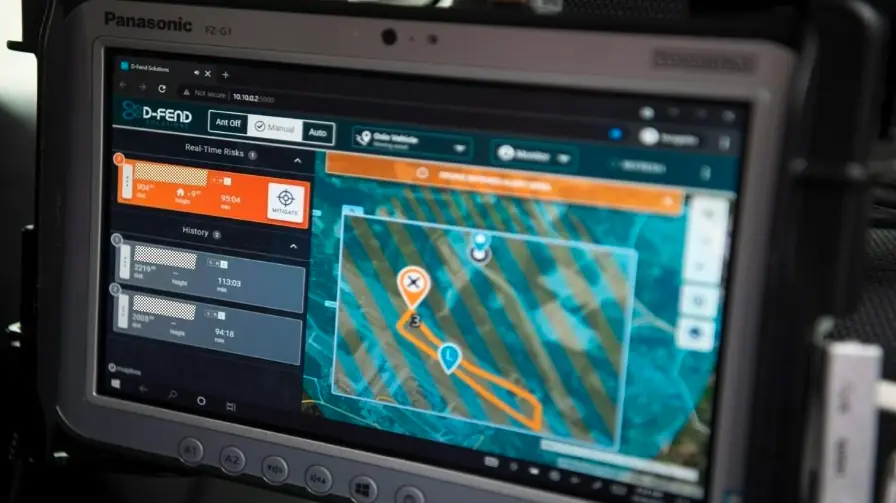
Leading C-UAS (counter unmanned aerial systems) developer D-Fend Solutions puts this new type of mitigation system to the test in the whitepaper: Cyber takedown – the next generation of more effective counter-UAS technology
The potential of using cyber-takeover methods rather than current and legacy counter-UAS technology is immense. Cyber-takeover methods can provide:
- Continuity of service as the incident is being managed (including authorized drone operations)
- Proportionality of response
- Considerable flexibility in defining the defensive envelope
- Precise analysis of incidents, which can be used for forensic reporting
The technology can be configured for both mobile and static applications and works in urban, built-up environments, plus it can be constantly updated to take account of new threat types.
Download the whitepaper in full from the D-Fend Solutions website >>










